System Security Plan Template
System Security Plan Template - This template is based on ssp requirements that are used for other us government compliance requirements for ssps, but it is tailored to document the entire controlled unclassified information (cui) environment for an organization. This includes all the system’s hardware, software, relevant personnel, etc. Each template must be customized to specifically address the system. More information about ssps can be found on the nist website. Specific system data shall be entered in the template when a colon symbol is indicated. Use this downloadable ssp template to develop an ssp for your organization. 1 system security requirements and describes controls in place or planned to meet those requirements. System security plan (ssp) template instructions. Enter data to the right of the colon symbol. This page provides a template and guidance to assist organisations in documenting their approach to managing and responding to cyber security incidents associated with their system(s) built on asd's blueprint for secure cloud. Use this downloadable ssp template to develop an ssp for your organization. The nist computer security resource center provides resources and templates for developing security plans to protect controlled unclassified information (cui) in nonfederal systems. It can be used for both public and private sector systems and applications, and it provides a baseline for developing an ssp. This template contains boiler plate language. Specific system data shall be entered in the template when a colon symbol is indicated. What cui is in regards to the company’s operations. Each template must be customized to specifically address the system. Two examples of how you can detail current implementation or planned implementation details for access control requirements Enter data to the right of the colon symbol. This page provides a template and guidance to assist organisations in documenting their approach to managing and responding to cyber security incidents associated with their system(s) built on asd's blueprint for secure cloud. This template is based on ssp requirements that are used for other us government compliance requirements for ssps, but it is tailored to document the entire controlled unclassified information (cui) environment for an organization. Specific system data shall be entered in the template when a colon symbol is indicated. Enter data to the right of the colon symbol. System security. What cui is in regards to the company’s operations. Two examples of how you can detail current implementation or planned implementation details for access control requirements This includes all the system’s hardware, software, relevant personnel, etc. 1 system security requirements and describes controls in place or planned to meet those requirements. Use this downloadable ssp template to develop an ssp. Specific system data shall be entered in the template when a colon symbol is indicated. A customizable template that's easy to tailor to your organization; Use this downloadable ssp template to develop an ssp for your organization. What cui is in regards to the company’s operations. The nist computer security resource center provides resources and templates for developing security plans. • appendix b provides a glossary of terms and definitions. Each template must be customized to specifically address the system. • appendix a provides a system security plan template. This includes all the system’s hardware, software, relevant personnel, etc. This template is based on ssp requirements that are used for other us government compliance requirements for ssps, but it is. • appendix b provides a glossary of terms and definitions. Each template must be customized to specifically address the system. This template is based on ssp requirements that are used for other us government compliance requirements for ssps, but it is tailored to document the entire controlled unclassified information (cui) environment for an organization. It can be used for both. Enter data to the right of the colon symbol. • appendix c includes references that support this publication. 1 system security requirements and describes controls in place or planned to meet those requirements. System security plan (ssp) template instructions. More information about ssps can be found on the nist website. A customizable template that's easy to tailor to your organization; System security plan (ssp) template instructions. • appendix a provides a system security plan template. Develop, document, and periodically update system security plans that describe system boundaries, system environments of operation, how security requirements are implemented, and the relationships with or connections to other systems. The nist computer security resource. 1 system security requirements and describes controls in place or planned to meet those requirements. Specific system data shall be entered in the template when a colon symbol is indicated. This template is based on ssp requirements that are used for other us government compliance requirements for ssps, but it is tailored to document the entire controlled unclassified information (cui). Enter data to the right of the colon symbol. Specific system data shall be entered in the template when a colon symbol is indicated. • appendix b provides a glossary of terms and definitions. Develop, document, and periodically update system security plans that describe system boundaries, system environments of operation, how security requirements are implemented, and the relationships with or. This includes all the system’s hardware, software, relevant personnel, etc. Use this downloadable ssp template to develop an ssp for your organization. This template is based on ssp requirements that are used for other us government compliance requirements for ssps, but it is tailored to document the entire controlled unclassified information (cui) environment for an organization. Two examples of how. System security plan (ssp) template instructions. What cui is in regards to the company’s operations. It can be used for both public and private sector systems and applications, and it provides a baseline for developing an ssp. • appendix a provides a system security plan template. Two examples of how you can detail current implementation or planned implementation details for access control requirements More information about ssps can be found on the nist website. Specific system data shall be entered in the template when a colon symbol is indicated. This includes all the system’s hardware, software, relevant personnel, etc. Enter data to the right of the colon symbol. A customizable template that's easy to tailor to your organization; • appendix c includes references that support this publication. Use this downloadable ssp template to develop an ssp for your organization. 1 system security requirements and describes controls in place or planned to meet those requirements. Develop, document, and periodically update system security plans that describe system boundaries, system environments of operation, how security requirements are implemented, and the relationships with or connections to other systems. • appendix b provides a glossary of terms and definitions. This page provides a template and guidance to assist organisations in documenting their approach to managing and responding to cyber security incidents associated with their system(s) built on asd's blueprint for secure cloud.Cmmc System Security Plan Template
20200508080812step All System Security Plan Template 3 Doc Template
Security Plan Template
FREE 8+ Sample Security Plan Templates in PDF MS Word Google Docs
System Security Plan Template
Cmmc System Security Plan Template
System Security Plan Template Doc Template pdfFiller
FREE 8+ Sample Security Plan Templates in PDF MS Word Google Docs
System Security Plan Ssp Template
MustHave System Security Plan Templates with Examples and Samples
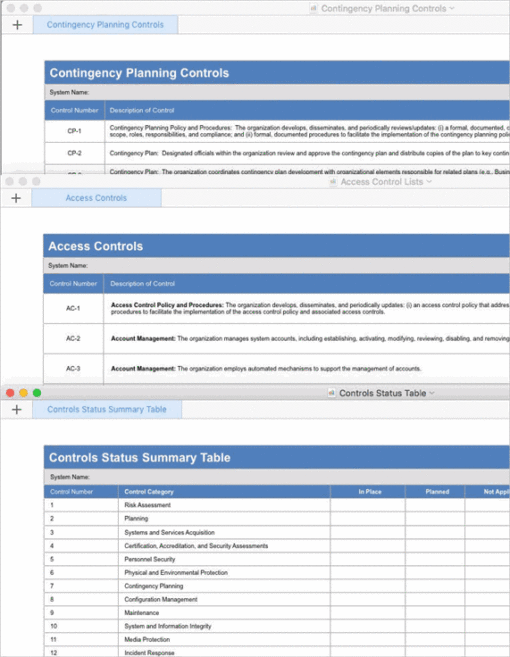
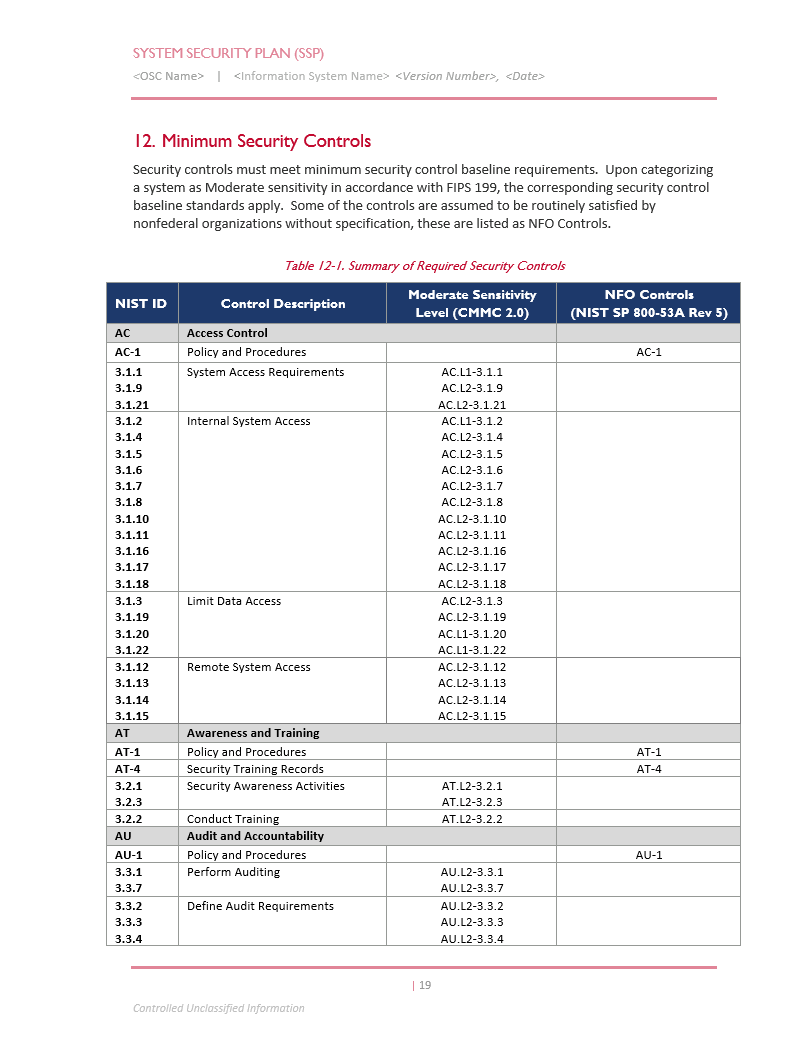
The Nist Computer Security Resource Center Provides Resources And Templates For Developing Security Plans To Protect Controlled Unclassified Information (Cui) In Nonfederal Systems.
Each Template Must Be Customized To Specifically Address The System.
This Template Is Based On Ssp Requirements That Are Used For Other Us Government Compliance Requirements For Ssps, But It Is Tailored To Document The Entire Controlled Unclassified Information (Cui) Environment For An Organization.
This Template Contains Boiler Plate Language.
Related Post: