Insider Threat Program Template
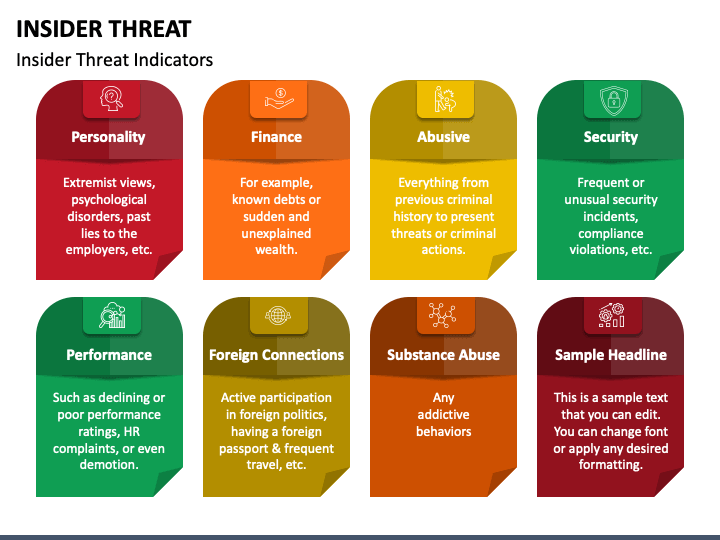
Insider Threat Program Template - Insider risk is the potential for an individual with access to an organization’s data resources to intentionally or accidentally perform an activity that negatively impacts the. Customizable insider threat program template, designed for federal contractors and local, state, and federal agencies. There are countless statistics about cybercrime and one of the most impactful is that for threat actors. Develop an insider threat program: As an example of an insider threat, in 2024,. The itp will seek to establish a secure. The itp will establish a secure operating environment for personnel, facilities, information,. Mplementing an insider threat management program (itmp). This guide supersedes the previous insider threat program guides issued by the nittf and ncsc including the nittf’s 2014 “guide to accompany the national insider threat policy and. Insiders can damage your company in countless ways, from destroying valuable equipment, to leaking sensitive data, to providing access to unauthorized third parties. Customizable insider threat program template, designed for federal contractors and local, state, and federal agencies. This guide supersedes the previous insider threat program guides issued by the nittf and ncsc including the nittf’s 2014 “guide to accompany the national insider threat policy and. Easily downloadable as an ms word file. Please click on the nittf technical page to review these bulletins. The program must gather, integrate, and report relevant and credible information covered by. This plan establishes policy and assigns responsibilities for the insider threat program (itp). The cybersecurity and infrastructure security agency (cisa) created these reporting templates as a tool for stakeholder organizations to download, review, and. This job aid explains how insider threat inquiries function within insider threat program operations. Once an organization has developed an insider threat program plan, it is essential to implement the plan and regularly review and update it. Insiders can damage your company in countless ways, from destroying valuable equipment, to leaking sensitive data, to providing access to unauthorized third parties. The itp will establish a secure operating environment for personnel, facilities, information,. This plan establishes policy and assigns responsibilities for the insider threat program (itp). Establish a formal program for identifying, mitigating, and responding to insider threats, including clear reporting mechanisms. It also describes the differences between an inquiry and an investigation. Develop an insider threat program: Their profits continue to increase year over year and are on track to rise from. The cybersecurity and infrastructure security agency (cisa) created these reporting templates as a tool for stakeholder organizations to download, review, and. Insider risk is the potential for an individual with access to an organization’s data resources to intentionally or accidentally perform an activity that negatively. Dod insider threat program template. This job aid explains how insider threat inquiries function within insider threat program operations. Insiders can damage your company in countless ways, from destroying valuable equipment, to leaking sensitive data, to providing access to unauthorized third parties. And mitigating the risk of an insider threat. An insider threat is any risk to your organization that. Please click on the nittf technical page to review these bulletins. The program must gather, integrate, and report relevant and credible information covered by. Dod insider threat program template. As an example of an insider threat, in 2024,. Nittf has developed technical bulletins that identify key technical issues in developing an insider threat program. There are countless statistics about cybercrime and one of the most impactful is that for threat actors. Dod insider threat program template. This plan establishes policy and assigns responsibilities for the insider threat program (itp). Insider threat to deter employees from becoming insider threats; Establish a formal program for identifying, mitigating, and responding to insider threats, including clear reporting mechanisms. Nittf has developed technical bulletins that identify key technical issues in developing an insider threat program. Once an organization has developed an insider threat program plan, it is essential to implement the plan and regularly review and update it. Insider risk is the potential for an individual with access to an organization’s data resources to intentionally or accidentally perform an. Their profits continue to increase year over year and are on track to rise from. Sample insider threat program plan for 1. This job aid explains how insider threat inquiries function within insider threat program operations. Establish a formal program for identifying, mitigating, and responding to insider threats, including clear reporting mechanisms. To establish and maintain an insider threat program. Easily downloadable as an ms word file. As an example of an insider threat, in 2024,. Establish a formal program for identifying, mitigating, and responding to insider threats, including clear reporting mechanisms. The itp will seek to establish a secure. Once an organization has developed an insider threat program plan, it is essential to implement the plan and regularly review. Mplementing an insider threat management program (itmp). Easily downloadable as an ms word file, helps you establish effective insider threat strategies in compliance with dod guidelines. Insiders can damage your company in countless ways, from destroying valuable equipment, to leaking sensitive data, to providing access to unauthorized third parties. Easily downloadable as an ms word file. Dod insider threat program. Insider threat to deter employees from becoming insider threats; Please click on the nittf technical page to review these bulletins. Customizable insider threat program template, designed for federal contractors and local, state, and federal agencies. Insiders can damage your company in countless ways, from destroying valuable equipment, to leaking sensitive data, to providing access to unauthorized third parties. Easily downloadable. The program must gather, integrate, and report relevant and credible information covered by. Establish a formal program for identifying, mitigating, and responding to insider threats, including clear reporting mechanisms. It also describes the differences between an inquiry and an investigation. This plan establishes policy and assigns responsibilities for the insider threat program (itp). The itp will seek to establish a secure. Once an organization has developed an insider threat program plan, it is essential to implement the plan and regularly review and update it. An insider threat is any risk to your organization that arises from an internal party’s access to your systems, assets, or data. Sample insider threat program plan for 1. To establish and maintain an insider threat program to detect, deter and mitigate insider threats. Insider risk is the potential for an individual with access to an organization’s data resources to intentionally or accidentally perform an activity that negatively impacts the. Easily downloadable as an ms word file. This plan establishes policy and assigns responsibilities for the insider threat program (itp). This guide supersedes the previous insider threat program guides issued by the nittf and ncsc including the nittf’s 2014 “guide to accompany the national insider threat policy and. Dod insider threat program template. As an example of an insider threat, in 2024,. The cybersecurity and infrastructure security agency (cisa) created these reporting templates as a tool for stakeholder organizations to download, review, and.Insider Threat Program Template
Insider Threat Program Template
Insider Threat Policy Template
Insider Threat Plan Template
Establishing a Foundation and Building an Insider Threat Program
Insider Threat Program Template
How to Establish an Effective Insider Threat Program
Insider Threat Program Template
Insider Threat Program Template
Insider Threat Program Template
The Itp Will Establish A Secure Operating Environment For Personnel, Facilities, Information,.
Nittf Has Developed Technical Bulletins That Identify Key Technical Issues In Developing An Insider Threat Program.
Customizable Insider Threat Program Template, Designed For Federal Contractors And Local, State, And Federal Agencies.
Insider Threat To Deter Employees From Becoming Insider Threats;
Related Post: