Data Security Policy Template
Data Security Policy Template - A data security policy is a set of guidelines and rules an organization establishes to manage and protect its data assets. Key elements of a cyber security policy. Standards a standard is set of prescribed practices or. The purpose of this policy is to outline the security measures that protect sensitive data within [your company name], ensuring the confidentiality, integrity, and availability of all. For a cyber security policy to be truly effective, it should cover the following essential areas: Navigate to security > conditional access. Understand what a data retention policy is and get templates, examples, and best practices for creating your own so you can minimize data exposure. “the policy separates data into four categories: You’ll find a great set of resources posted here already, including it security policy templates for thirteen important security requirements based on our team’s recommendations. The templates can be used as an outline of an organizational policy, w. It resources typically include hardware (computers, servers, peripherals), software (licensed applications,. This sample policy is for. Resource center / sample data protection policy template. What are the policies for data sharing, including, where applicable, provisions for protection of privacy, confidentiality, intellectual property, national security or other rights or requirements?. Policies on encryption, access control, and other security practices. Configure conditional access policy to evaluates the custom attribute. The purpose of this policy is to outline the security measures that protect sensitive data within [your company name], ensuring the confidentiality, integrity, and availability of all. To create a robust information security policy, organizations need to consider several key information security standards that address different aspects of data protection. You’ll find a great set of resources posted here already, including it security policy templates for thirteen important security requirements based on our team’s recommendations. Get a step ahead of your cybersecurity goals with our comprehensive templates. “the policy separates data into four categories: For a cyber security policy to be truly effective, it should cover the following essential areas: The purpose of this policy is to outline the security measures that protect sensitive data within [your company name], ensuring the confidentiality, integrity, and availability of all. You’ll find a great set of resources posted here already,. Our list includes policy templates. These are free to use and fully customizable to your company's it security practices. This sample policy is for. What are the policies for data sharing, including, where applicable, provisions for protection of privacy, confidentiality, intellectual property, national security or other rights or requirements?. It resources typically include hardware (computers, servers, peripherals), software (licensed applications,. Resource center / sample data protection policy template. With a free data security policy template from jotform sign, you can create a custom policy, send it to involved parties to sign on any device, and store your documents as handy pdfs for. Standards a standard is set of prescribed practices or. Sans has developed a set of information security policy. Key elements of a cyber security policy. Standards a standard is set of prescribed practices or. White fuse has created this data protection policy template as a foundation for smaller organizations to create a working data. With a free data security policy template from jotform sign, you can create a custom policy, send it to involved parties to sign on. Get a step ahead of your cybersecurity goals with our comprehensive templates. Standards a standard is set of prescribed practices or. Navigate to security > conditional access. To create a robust information security policy, organizations need to consider several key information security standards that address different aspects of data protection. Resource center / sample data protection policy template. Financial data, customer information, employee personal data, and proprietary data. Get a step ahead of your cybersecurity goals with our comprehensive templates. It resources typically include hardware (computers, servers, peripherals), software (licensed applications,. These are free to use and fully customizable to your company's it security practices. Policies on encryption, access control, and other security practices. Configure conditional access policy to evaluates the custom attribute. For a cyber security policy to be truly effective, it should cover the following essential areas: These are free to use and fully customizable to your company's it security practices. It resources typically include hardware (computers, servers, peripherals), software (licensed applications,. A data security policy is a set of guidelines and. A data security policy is a set of guidelines and rules an organization establishes to manage and protect its data assets. It resources typically include hardware (computers, servers, peripherals), software (licensed applications,. Configure conditional access policy to evaluates the custom attribute. The purpose of this policy is to outline the security measures that protect sensitive data within [your company name],. What are the policies for data sharing, including, where applicable, provisions for protection of privacy, confidentiality, intellectual property, national security or other rights or requirements?. Our list includes policy templates. Standards a standard is set of prescribed practices or. Understand what a data retention policy is and get templates, examples, and best practices for creating your own so you can. This policy outlines how the company's data should be. Open the entra admin center. Get a step ahead of your cybersecurity goals with our comprehensive templates. These are free to use and fully customizable to your company's it security practices. Resource center / sample data protection policy template. Resource center / sample data protection policy template. It resources typically include hardware (computers, servers, peripherals), software (licensed applications,. White fuse has created this data protection policy template as a foundation for smaller organizations to create a working data. A data security policy is a set of guidelines and rules an organization establishes to manage and protect its data assets. “the policy separates data into four categories: Configure conditional access policy to evaluates the custom attribute. Key elements of a cyber security policy. Understand what a data retention policy is and get templates, examples, and best practices for creating your own so you can minimize data exposure. Sans has developed a set of information security policy templates. Create a new policy and. Get a step ahead of your cybersecurity goals with our comprehensive templates. These are free to use and fully customizable to your company's it security practices. This policy outlines how the company's data should be. Open the entra admin center. Standards a standard is set of prescribed practices or. You’ll find a great set of resources posted here already, including it security policy templates for thirteen important security requirements based on our team’s recommendations.42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
Data Protection Policy Template Free Download Easy Legal Docs
Free Printable Security Policy Templates [PDF, Word] Information
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
FREE 8+ Security Policy Samples in MS Word PDF
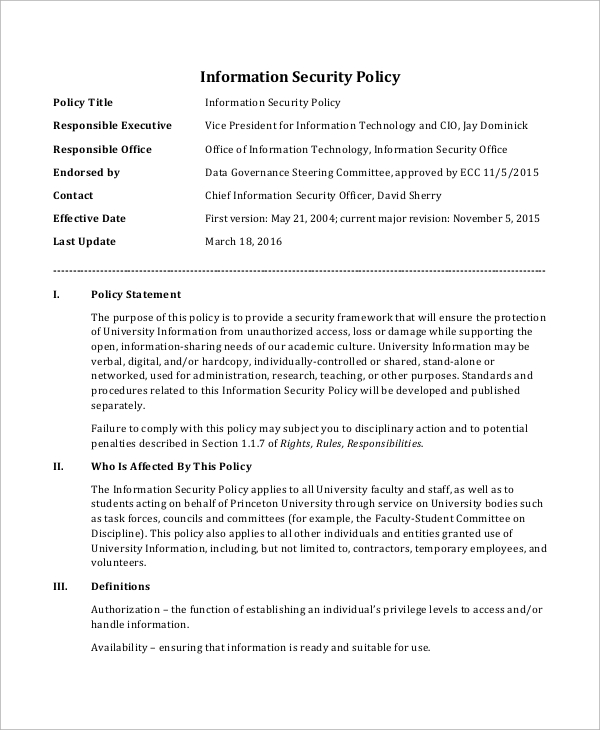
20+ Free Information Security Policy Templates [Word, PDF] » TemplateData
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
Financial Data, Customer Information, Employee Personal Data, And Proprietary Data.
Policies On Encryption, Access Control, And Other Security Practices.
Our List Includes Policy Templates.
The Purpose Of This Policy Is To Outline The Security Measures That Protect Sensitive Data Within [Your Company Name], Ensuring The Confidentiality, Integrity, And Availability Of All.
Related Post:
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-11.jpg)
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-34.jpg)

![Free Printable Security Policy Templates [PDF, Word] Information](https://www.typecalendar.com/wp-content/uploads/2023/05/Information-security-policy-examples.jpg?gid=207)
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-10.jpg)
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-02.jpg)
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](http://templatelab.com/wp-content/uploads/2018/05/Security-Policy-13.jpg)
![20+ Free Information Security Policy Templates [Word, PDF] » TemplateData](https://templatedata.net/wp-content/uploads/2021/07/free-information-security-policy-template-1.jpg)
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-22.jpg)