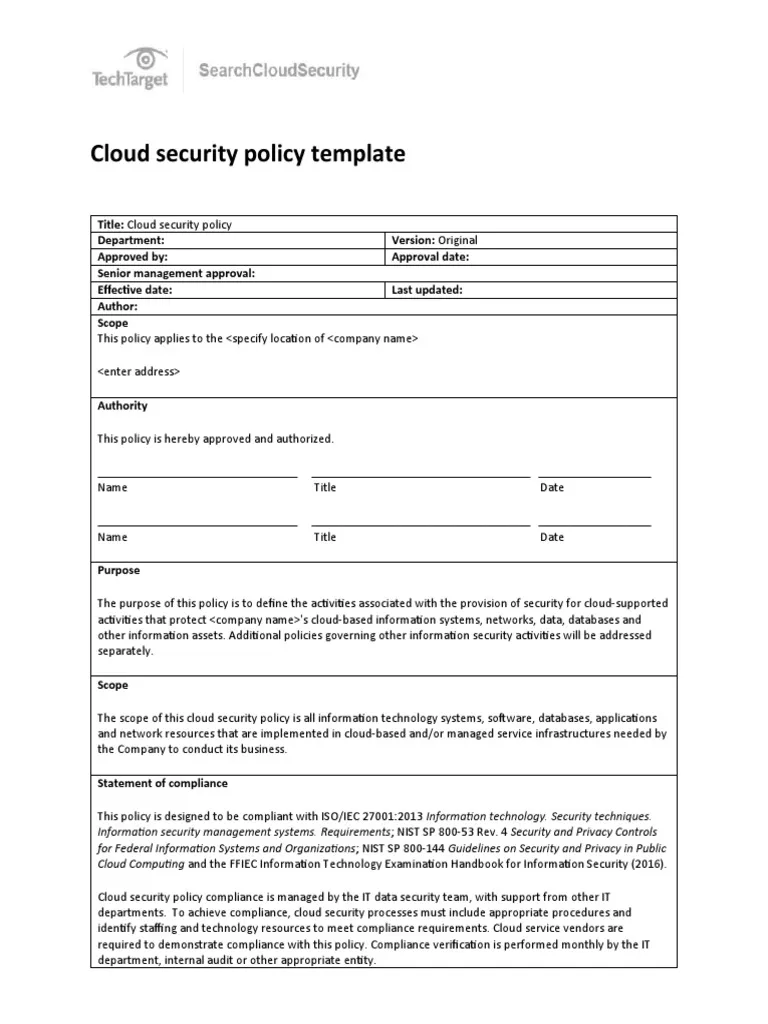
Cloud Security Policy Template
Cloud Security Policy Template - Our list includes policy templates. Use this template to protect your data and ensure efficient cloud. This cloud security policy template pdf provides a comprehensive framework for developing secure cloud architecture. Sans has developed a set of information security policy templates. It defines the purpose, scope, and compliance standards for securing cloud systems and data. This document provides a template for creating a cloud security policy. Are requested, tested, approved and communicated for audit and recordkeeping purposes. My customizable cloud security strategy policy template provides the guidance and framework you need to develop a comprehensive and tailored approach to cloud security. With this template you will be able to: A cloud security policy is a set of rules and guidelines that govern how an organization's cloud environment and the data within it is. What is a cloud security policy? Having a cloud security policy template is essential for any organization that will be using cloud computing services. This cloud security policy template pdf provides a comprehensive framework for developing secure cloud architecture. The purpose of this cloud security policy, written by ray fernandez for techrepublic premium, is to provide guidelines for secure and effective cloud computing. Sans has developed a set of information security policy templates. Our list includes policy templates. Iain mulholland, senior director, security engineering, shares insights on the state of ransomware. Download a template to get the process started. Use this template to protect your data and ensure efficient cloud. These are free to use and fully customizable to your company's it security practices. With this template you will be able to: This cloud security policy template pdf provides a comprehensive framework for developing secure cloud architecture. Effective cloud security means more than implementing strong access and authentication controls or encrypting data at rest. Iain mulholland, senior director, security engineering, shares insights on the state of ransomware. Key elements of a comprehensive cloud computing. My customizable cloud security strategy policy template provides the guidance and framework you need to develop a comprehensive and tailored approach to cloud security. Having a cloud security policy template is essential for any organization that will be using cloud computing services. Effective cloud security means more than implementing strong access and authentication controls or encrypting data at rest. This. Define roles and responsibilities during an incident, including communication protocols. The purpose of this cloud security policy, written by ray fernandez for techrepublic premium, is to provide guidelines for secure and effective cloud computing. Use this template to protect your data and ensure efficient cloud. Effective cloud security means more than implementing strong access and authentication controls or encrypting data. Understand what a data retention policy is and get templates, examples, and best practices for creating your own so you can minimize data exposure. Download a template to get the process started. Welcome to the second cloud ciso perspectives for january 2025. Are requested, tested, approved and communicated for audit and recordkeeping purposes. My customizable cloud security strategy policy template. This policy addresses all bkt pay technology, systems, data and networks implemented in private,. With this template you will be able to: This document provides a template for creating a cloud security policy. Effective cloud security means more than implementing strong access and authentication controls or encrypting data at rest. Use this template to protect your data and ensure efficient. In this guide, we’ll break down how to create a cloud security policy and provide a free template to help you get started. Having a cloud security policy template is essential for any organization that will be using cloud computing services. This document provides a template for creating a cloud security policy. Understand what a data retention policy is and. Iain mulholland, senior director, security engineering, shares insights on the state of ransomware. This document provides a cloud security policy for a company. Sans has developed a set of information security policy templates. These are free to use and fully customizable to your company's it security practices. Our list includes policy templates. Define roles and responsibilities during an incident, including communication protocols. Are requested, tested, approved and communicated for audit and recordkeeping purposes. Iain mulholland, senior director, security engineering, shares insights on the state of ransomware. Welcome to the second cloud ciso perspectives for january 2025. Our list includes policy templates. Our list includes policy templates. This policy addresses all bkt pay technology, systems, data and networks implemented in private,. It outlines key sections such as purpose, scope, roles and responsibilities, acceptable usage, approved and. What is a cloud security policy? Understand what a data retention policy is and get templates, examples, and best practices for creating your own so you. This document provides a cloud security policy for a company. It outlines key sections such as purpose, scope, roles and responsibilities, acceptable usage, approved and. Are requested, tested, approved and communicated for audit and recordkeeping purposes. Having a cloud security policy template is essential for any organization that will be using cloud computing services. It defines the purpose, scope, and. Iain mulholland, senior director, security engineering, shares insights on the state of ransomware. This cloud security policy template pdf provides a comprehensive framework for developing secure cloud architecture. What is a cloud security policy? These are free to use and fully customizable to your company's it security practices. Having a cloud security policy template is essential for any organization that will be using cloud computing services. Download a template to get the process started. Use this template to protect your data and ensure efficient cloud. A cloud security policy is a set of rules and guidelines that govern how an organization's cloud environment and the data within it is. The purpose of this cloud security policy, written by ray fernandez for techrepublic premium, is to provide guidelines for secure and effective cloud computing. Define roles and responsibilities during an incident, including communication protocols. It outlines key sections such as purpose, scope, roles and responsibilities, acceptable usage, approved and. Sans has developed a set of information security policy templates. Our list includes policy templates. Effective cloud security means more than implementing strong access and authentication controls or encrypting data at rest. Welcome to the second cloud ciso perspectives for january 2025. This policy addresses all bkt pay technology, systems, data and networks implemented in private,.A Comprehensive Cloud Security Policy Template to Safeguard
The Ultimate ISO 27001 Cloud Services Security Policy Template
IT Cloud Security Policy Template in Word, PDF, Google Docs Download
Cloud Security Policy Template PDF Information Security Security
IT Cloud Security Policy Template in Word, PDF, Google Docs Download
IT Cloud Security Policy Template in Word, PDF, Google Docs Download
The Ultimate ISO 27001 Cloud Services Security Policy Template
The Ultimate ISO 27001 Cloud Services Security Policy Template
IT Cloud Security Policy Template in Word, PDF, Google Docs Download
The Ultimate ISO 27001 Cloud Security Policy Template
In This Guide, We’ll Break Down How To Create A Cloud Security Policy And Provide A Free Template To Help You Get Started.
Key Elements Of A Comprehensive Cloud Computing Security Policy Template Include Scope And Applicability, Data Protection, Access Control, Network Security, And Incident Response.
Are Requested, Tested, Approved And Communicated For Audit And Recordkeeping Purposes.
It Defines The Purpose, Scope, And Compliance Standards For Securing Cloud Systems And Data.
Related Post: